Data Risk Management Part 2: Data Security Platform
Data security strategies for the discovery, monitoring, and protection of data and privacy
About
The webinar discusses data security strategies and their relevance to discovering, monitoring, and protecting data and privacy. We will look at the data risk approach to DLP – the next generation of DLP strategies.

Safeguarding business data assets in hybrid environments can pose significant challenges. The data lifecycle is often not fully comprehended and fails to comply with data protection regulations and laws. This can lead to various data risks, such as data loss that can compromise the confidentiality and accessibility of the data, unauthorized access to data that can jeopardize its confidentiality, unauthorized modifications that can affect data integrity, data protection compliance breaches that can compromise the confidentiality and privacy of the data subject, and many other scenarios that can pose risks to data.
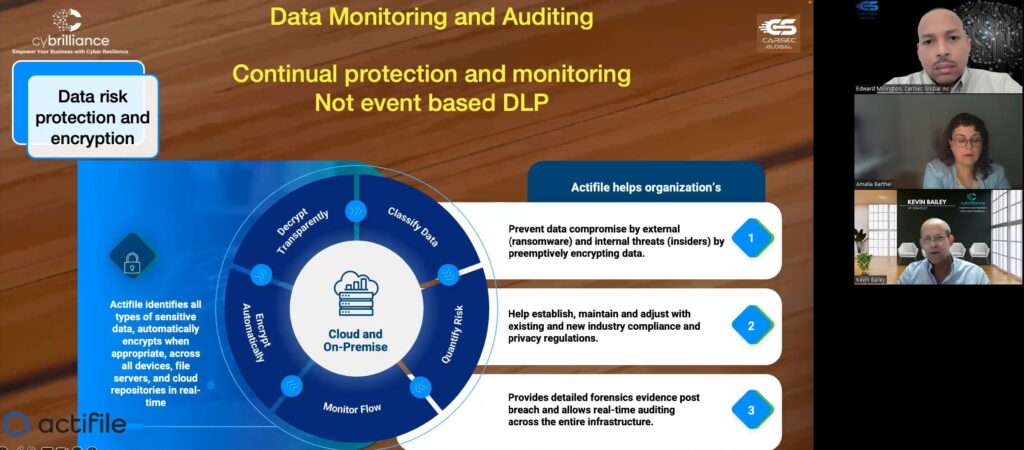
To ensure maximum data security, it is crucial to have a clear understanding and visual view of how data flows through data monitoring. This becomes even more important in a breach when cyber attackers have exfiltrated data. In such situations, responding appropriately, informing authorities, and complying with legal requirements is essential. For this, you must know what data was exfiltrated, when it happened, and the amount of data involved. To provide data assurance, continuous real-time visibility is necessary.
Discussion points:
- Data Risk Management: 3-Step Approach
- Data Risk Discovery and Quantification
- Data Risk Monitoring and Auditing
- Data Risk Remediation by Encryption
Who should attend:
- DPO
- Risk Managers
- Compliance
- CISO
- CTO
- CIO
- Data Protection Professionals
- Legal Advisors
- DataCenters Managers/Administrators
- Security Directors
- Security Managers
- IT Directors
- IT Managers
- IT Professionals
- Business Strategists
- ICT Strategists
- IT Leaders
- Senior IT Personnel
- IT Specialist
- Senior Network Administrators
- Anyone interested in Cybersecurity, Cyber Resilience, Data Resilience, Data Protection, Data Privacy, etc.