
Caribbean State of Cyber Security
CariSec Global Inc was featured in Barbados Today enewspaper column providing the cybersecurity awareness on the topic of “Caribbean State of Cyber Security”
The Caribbean region continues to see an explosion of Digital Transformation and the use of technology in an integral way in the advancement of human development. But in today’s criminal enterprised world, being connected comes with vast cyber risks where connected systems are constantly under attack by cyber-criminals for data exfiltration, ransom, and the disruption of services and functions.
When one thinks of all the cyberattacks that have been going on over the last few years, especially in today’s current frequency, one wonders why businesses are being affected with all the “technological security” employed and why it seems so impossible to defend against these attacks, and from being compromise and breach. Many cyber-attacks come in the form of Malware, Ransomware, Phishing, Business Email Compromise, exploitation of vulnerable unpatched technologies, etc., all making up the Threat Landscape the business operates in. The following paragraphs will discuss why this problem exists and why it will continue, costing businesses greater financial and operational losses, until the culture changes in the region to one of a security nature.
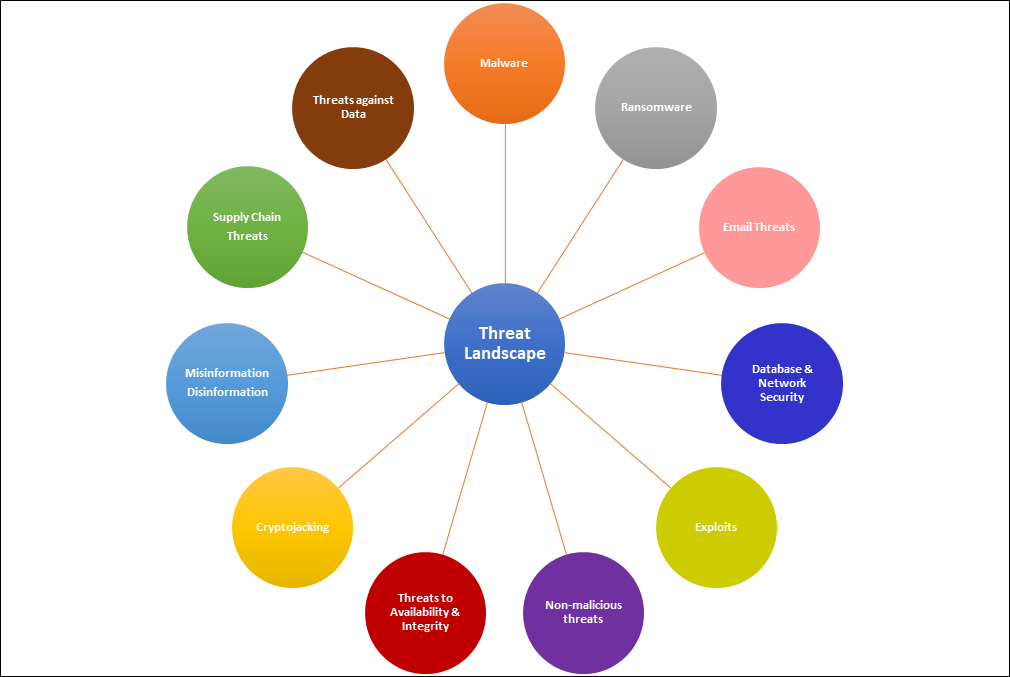
Between the latter half of 2021 and the first quarter of 2022, we have seen several global Threat Reports highlighting the growing Cybersecurity Risks many business sectors had faced and are predicted to face: Public, Health, Financial, Retail, Private, etc. These reports provide Cyber Threat Intelligence (CTI) to businesses, enabling Boards, Business Executives, and Business Owners in reducing operational risks, through risk-based decisions in their cyber defense again cyber-criminals. This occurs when CTI effect changes within the business’ risk management program and resulting security controls in the reduction of risks to cyber-threats.
While such reports may not be available or known to everyone within the business community, the constant media awareness on the topic cannot go unnoticed and one wonders how well this topic is considerably understood to be acted upon, where the security of businesses is increased in respect to the type of threats it may face, preventing the success of a cyber-attack and or a breach, which can lead to substantial financial, operational, reputational, transactional and other losses, affecting the business immensely.
Cybersecurity is one topic that is not well understood and in many instances, treated as IT security and or the responsibility of IT. It must be noted that many of the security controls (previously mentioned) are applied in IT, but cybersecurity is not an IT issue but a strategy ordained by the organisation’s governance program and effective throughout the whole business or the organization. This must be understood and made clear! The strategy is aligned to the business vision, strategic objectives, and goals and in so doing, should be driven by business leaders from top to bottom, enhancing and improving cyber security maturity to the highest capability level, determined by the risk appetite of the business/organization.
To improve the cyber security maturity posture of the business, the implementation of an Information Security Governance Program is required to manage every component of security that affects the organization, its people, process, and technology. The program, operating as an integral part of the business, drives the policies that institute many of the security controls that are needed in the risk treatment of cyber risks. Such a program exists in very mature Enterprises, the financial and military sectors, and others. Its maturity is governed by the organisation’s risk management program maturity and through risk strategies, its design is more refined in managing security.
But with respect to the current cyber-attack reports from businesses, this program does not seem to be operating well. While a business may be compromised or suffer a breach at some point in its history, the forensic review of the attack always shows some breakdown in security. That is, the security controls implemented and operated may be ineffective, inefficient, and or insufficient in treating cyber risk(s). Such compliance comes into question in how fluid the program is to the threat landscape and CTI in the treatment of new cyber risks.
The Information Security Governance Program is always affected by:
- The C-Suite (board/business executives/business owners) inability to understand what is cybersecurity and the risk cyber threats posed to the business. This situation arises when the executive group believes that Cybersecurity is IT Security (for which it is not) and IT-related matters are not the concern of the C-Suite. In addition, not supporting cybersecurity programs in their entirety throughout the organization, affects building security-aware cultures.
- The Enterprise Risk Management Program or some form of it, does not take into consideration Cyber Risks. This could imply risk management activities and processes in determining Cyber risks may not be carried out or used in building a very mature program.
- The use of CTI in the risk management process is either unavailable, not concise, or not utilized at all, especially if it is not understood of its importance to the threat landscape.
- Cybersecurity Risk Assessments are not carried out frequently, especially in an agile environment to determine new risks to the business, as the business digitally transforms.
- Unskilled human resources who are not security trained or cyber security-aware in their duties in supporting the program.
- Programs policies are not supported and enforced by stakeholders. This can lead to unauthorized changes, use of prohibited software, operation of unpatched systems, systems not security-hardened in production, incorrect and inappropriate technologies used in the identification, detection, protection, response, and recovery to cyber incidences, etc.
The cybersecurity challenges to the Caribbean are extraordinary and with limited resources, security strategies are key in the security operations of organisations/businesses. Regional to National Cybersecurity Strategies are also critically needed to guide and aid in the awareness, protection, and safety of the Digital society, where data is protected and kept confidential, and available at all times with a high level of integrity to carry out business at all levels. To meet and exceed these challenges, including meeting Data Protection Laws, businesses/organisations must implement Risk-based Information Security Governance Programs in the security operations of all areas of their digital businesses for secure operations.






