Combatting everyday Endpoint Exploits!
Todays’ businesses continues to face an ever increasing threat of vulnerable systems (many times, recently discovered – Zero-Day) exploited for Ransom and Information by Cyber Criminals. The rate of vulnerabilities seems to be increasing “exponentially” and the ability to keep up to date by a Patch Program is exhausting and in many cases futile. This then begs the question what can businesses do to improve their Cybersecurity Maturity Posture to mitigate these Zero-Day Threats.
Exploited vulnerabilities in the news:
Apache Log4j Vulnerability
CISA Emergency Directive: Patch ‘PrintNightmare’ Flaw (govinfosecurity.com)
Microsoft discovers critical SolarWinds zero-day under active attack | Ars Technica
Inappropriate/Ineffective Security Controls: Many business Security Governance Programs are not very well developed and or updated, leading to the inability of ineffective and inefficient Risk Treatment processes to threats. That is, not having the appropriate and effective levels of Security Controls (SC) in place to mitigate and or reduce the attack surface in times of a compromise and or a breach. So how do we enhance the Security Operational Maturity Level(s) to automate (to say the least) in the mitigation of threats at all levels on the Endpoint – carried out by todays’ Threat Actors (TA’s)?
Proactive, not Reactive: Businesses utilising stagnant Information Security Programs, find themselves implementing SC’s that are inappropriate in mitigating threats. That is, using Signature-based Antivirus Solutions or Malware scanning tools or some old technique to fight against TA’s using todays Tactics, Techniques and Procedures as described and highlighted by the MITRE ATT@CK Framework.
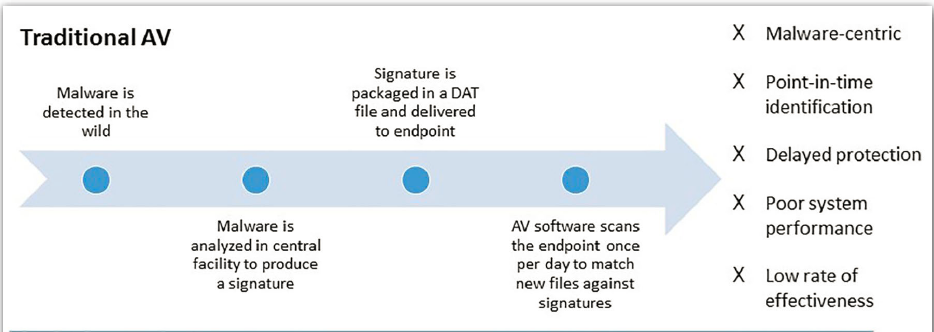
These tools are reactive and not proactive in mitigating attacks at the early stages of the Kill Chain Cycle, as shown below. Not only ineffective but impacting gravely on the performance of endpoints from constantly scanning and tying up of critical resources, affecting Users’ performance thereby hindering businesses efficiencies. So how can businesses mitigate at the first three(3) stages of the Kill Chain Cycle?
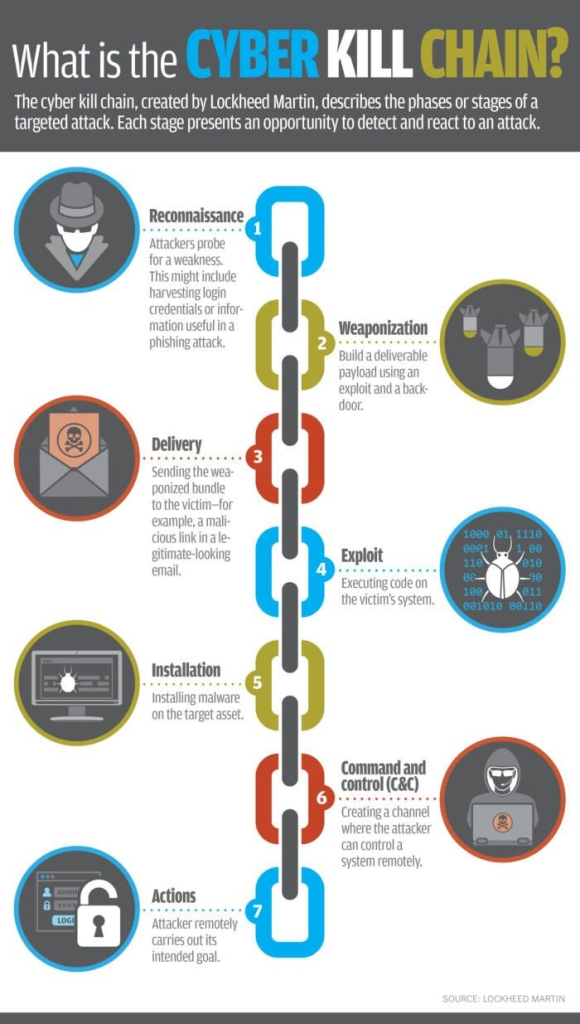
Proactive Mitigation Solution Requirements: To mitigate such threats early in the Kill Chain Cycle, businesses should review and carry out Proof-of Concepts (POC’s) on solutions with the following requirements to achieved effective and efficient, well designed Security Controls:
- Great Threat Detections – Review MITRE ATT@CK EDR Evaluation
- Response to threats quickly and early in the Kill Chain Cycle as much possible – small dwell times.
- Utilised ML (Supervised and Unsupervised) and AI to detect threats and anomalies
- Offer the ability to adequately and actively investigate BIOC’s, IOC’s and TTP’s for risk treatment and threat intelligence. This is very important when a compromised and or breach occurs for Incident Management and also in the creation of Incident Response Plans.
- Utilising additional functions, processes and controls as show below in addition to Credential Theft Protection.
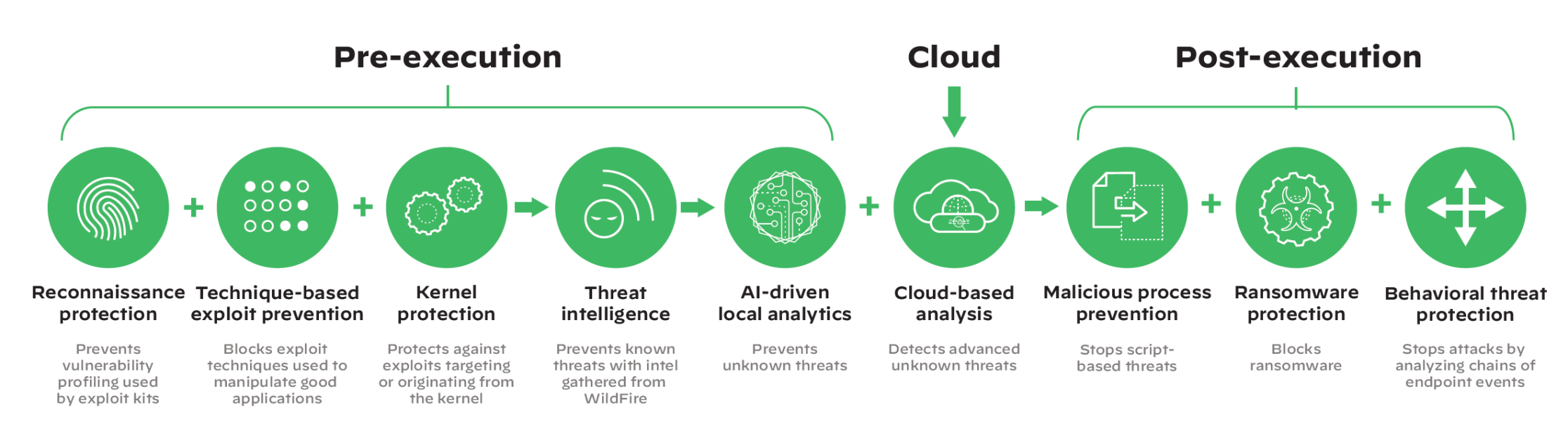
Endpoint Solution: To mitigate such threats early in the Kill Chain Cycle implies the implementation of an XDR Solution. Why XDR? You need to utilised all administrative and technical sensors for better Threat Intelligence and Response, from every area of the business. Please see review the video’s below:
Recommended Solution: Palo Alto Networks Cortex XDR, BlackBerry Cylance, Sentinel One are some of the key solutions to look at in the defense and protection of your business. To verify if such a solution is adequate, it is important to carry out a Proof-of-Concept determining if such a solutions meets your IT & Security Strategy needs.
CariSec Global also provides the MDR Service with additional components, managing your entire network, increasing your Cybersecurity posture in many ways.
Additional Information Sharing Links:
- https://www.linkedin.com/posts/edwardmillington_this-is-how-long-hackers-will-hide-in-your-activity-6805600331293171712-FZEG
- Cybersecurity Maturity Models (hhs.gov)
- https://www.linkedin.com/posts/edwardmillington_cis-controls-navigator-cis-activity-6806559616810446848-uCjH
- https://www.linkedin.com/posts/edwardmillington_issp-iet-ciisec-activity-6820519832727937024-KSUP
- https://www.linkedin.com/posts/edwardmillington_globalcybercrisis-frameworks-securityawareness-activity-6820696308383313921-UiY2
- https://www.linkedin.com/posts/edwardmillington_why-your-vulnerability-management-strategy-activity-6805075414306865152-NPo3
- https://www.linkedin.com/posts/edwardmillington_ransomware-gangs-get-paid-off-as-officials-activity-6813047484491853824-SkwN
- https://www.linkedin.com/posts/edwardmillington_endpoint-security-is-a-double-edge-sword-activity-6810502830160437248-z6ll
- https://www.linkedin.com/posts/edwardmillington_caribbeansecurityforum-caribbean-caribbeansecurityorganisations-activity-6808338977167335424-AZRY






