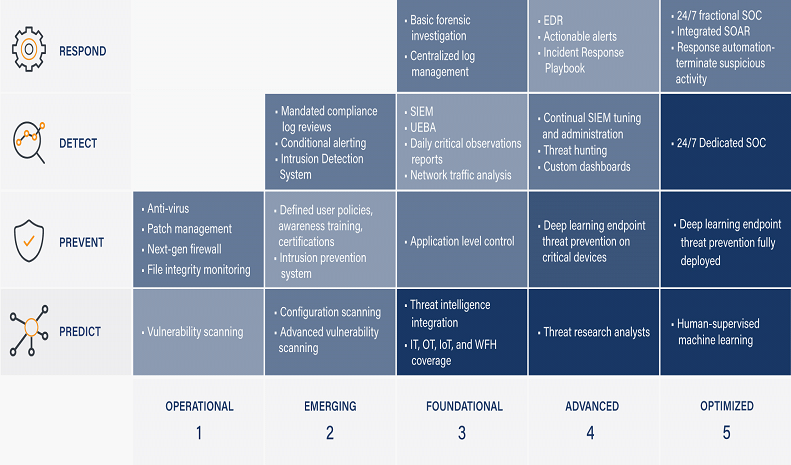
In response to (Protecting infrastructure: it’s impossible to always stay alert | Cybernews), protecting Critical Infrastructures (CI) takes a multistep methodology approach to cover all risk areas of operations and the management of those risks as highlighted in many standards: NIST SP 800-82 Rev 2, ISA/IEC 62443, NIST SP 800-37 Rev 2, ISO/IEC 27005, etc. […]
In a recent article written by the Managing Director of CariSec Global Inc. – “Why businesses continue to fail Cyber Security!“, one can understand the need to have matured risk-based Information & Cyber Security Program implemented and operated with the goal of CIAS (Confidentiality, Integrity, Availability and Safety) – all aim in protecting the Organisation […]
A Security Breach is the Unauthorized Access to an Organization Structure(s) to gain access to Systems, Data, Information, Resources, etc. to carry out Cyber Criminal Activity, affecting the CIA triage and in some cases, operational safety.